Cyber attacks and information security
The history of computer viruses starts from 1983 when the American scientist Fred Cohen for the first time introduced the term. Since then the dictionary has acquired dozens of scary terms from the area of digital technology: worms, viruses, malware (two-faced malware), pseudo-antiviruses, blastware, jailbreaking (acquiring full access to iOS device), ghostware, or cracking accounts in social media networks.
 Most wanted cyber criminals
Most wanted cyber criminalsAll these horrible terms are not harmless concepts but rather powerful and comprehensive tools of modern hackers. The specialists agree that today cyber attacks are focused not only on personal computers and corporate computer networks but on critically important infrastructural objects, any equipment that is part of remote control systems.
Protection from cyber attacks and cyber terrorism is now a part of the defense strategy of many countries. This is done for a good reason. The US Government spends nearly 8 billion dollars on information security. Well-publicized events of cyber attacks on large corporations frequently and routinely entertain the public. However, more than 70 percent of organizations are keeping quiet about similar incidents trying not to scare investors and shareholders. Therefore the information about cyber attacks that appears in mass media is just a tiny part of all such incidents and cyber cracks.
It was observed that Britain encounters nearly 1000 cyber attacks every hour. According to Arne Shenbom (an interview to the newspaper Bild), the head of the Cyber Security Council in Germany, cyber attacks on government institutions in Germany are becoming more and more inventive and effective.
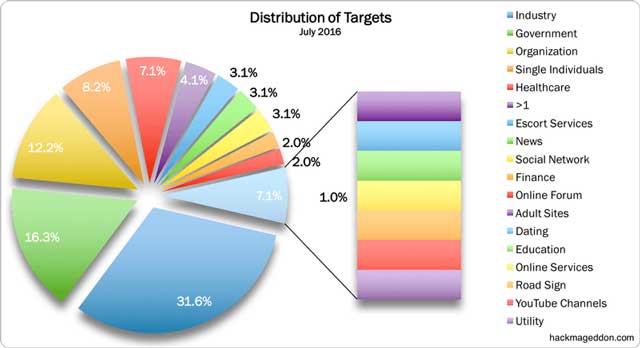
Distribution of Targets in July 2016
The Kremlin has to withstand several hundred of cyber attacks every day, the attempts to crash the computer systems involved in regular direct lines with Vladimir Putin are made primarily from abroad, says Dmitry Peskov, Press secretary of the President of Russia.
The analytic company Gartner specializes in studying the spread of digital technologies in business environment. The company announced that in 2016 it will prioritize the following topics:
- machines and their role in assisting humans;
- machines as a source of information for decision making;
- digital innovations for consumers.
Such approach of the analytical company is justified by the ever growing number of digital devices in use. From 2015 the number of network-connected devices grew by 30% and reached slightly under 7 billion pieces. In another 10 years that number will probably exceed 20 billion. Imagine what a wide field of action for this-day and future hackers!
This is one of the reasons why conferences in the area of information security are being regularly held all over the world. Specialists are trying to work out acceptable methods of counteracting the threat that is hanging over the digital community. In fact, such conferences are organized not only by government institutions and specialists fighting digital crimes but by hackers as well.
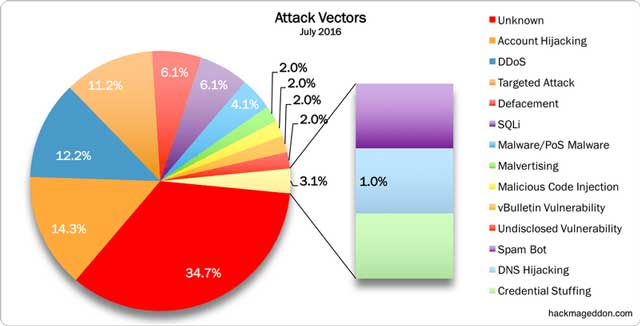
Attack Vectors July 2016
For example, the famous Def Con, annual conference of hackers in Las Vegas, in 2016 attracted more than 12 thousand participants. Prior to the opening of the Conference, another event was held in Las Vegas: the conference Black Hat with the participation of the so called “black hackers” who specialize on cracking computer data bases.
According to Associated Press, one of the participants made a presentation that demonstrated how negligent were the majority of PC users when it came to matters of Internet security. In preparation to the report a group of activists “left” flash drives with the potentially dangerous software in shops, on park benches and other such public places. In the 80% of cases the “lucky” people who found flash drives would start using them in their own PCs without any attempt to run the anti-virus scan or format the newly-found drives. This is in Russia various agencies are trying to run educational programs aimed at raising the media-literacy of the population.
Today almost all critical civilian infrastructural services – water, energy, heating, transport, medical services – are connected via the Internet. Unfortunately, all these networks are very vulnerable to cyber attacks. To protect civilian digital networks from cyber terrorists is one of the critically important task of every state.





